With the recent series of security breaches on many popular web services, Cyber criminals have proved that nothing on the internet is secure nowadays. When hackers can easily hack into the Email accounts of millions of Yahoo users, Gmail on the other hand might not be hundred percent hack proof.
Its not only the hackers that can hack and access your private data in Gmail, even people with personal vendetta against you can make use of methods such as social engineering and key-loggers to steal your account login details and gain access into your Gmail account. Most of the time these things happen silently without your knowledge, which is why Google has provided at your disposal, an easy way to check whether your Gmail account was compromised or not. Here’s how you can check whether you Gmail account was compromised or not.
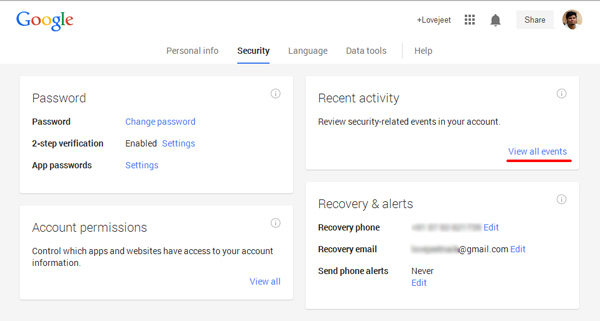
- Step 1: Head over to https://www.google.com/settings/security
- Step 2: Click on View all events in the Recent activities section.
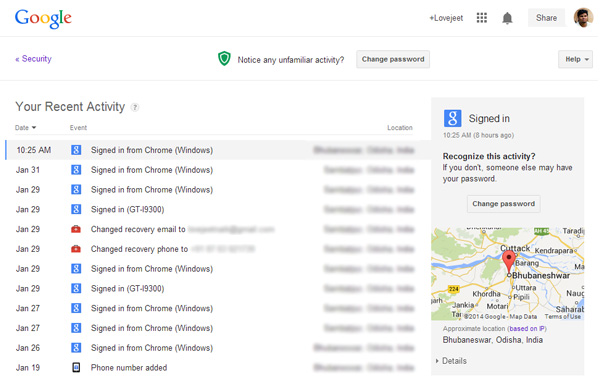
- Step 3: Now you can view the recent activities in your Gmail account, which you show you when and where was your Google account accessed from, including the details if your account was accessed from a computer, smartphone, tablet or any other devices along with the apps or web browsers used.
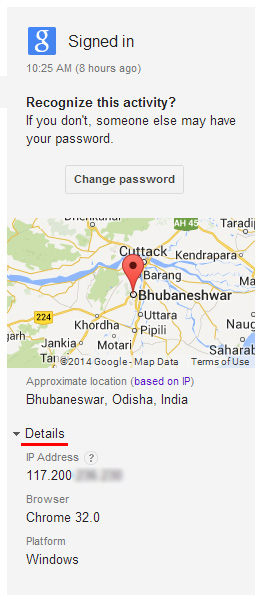
- Step 4: Select all the event individually and check the location details provided. Click on details below location data to see the IP address of the computer or device from which your Gmail account was accessed from.
The location data shown is calculated approximately, which is why you don’t need to panic if you see a location that’s a few kilometers away from you. What you need to see is the IP address range, which will let you know whether somebody else apart from you has access to your Gmail account.
Check out all the events carefully and if you see any suspicious IP address and location, you might need to change your password immediately. Last but not the least, I would suggest you to enable the Two-factor authentication system and ensure that you use a strong password with combinations of both words, numbers and special symbols.